In this article I would like to show you how to set up MFA Authentication on your Citrix ADC / Netscaler Azure. This article is part of the series about the different authentication methods you can use on your Citrix ADC / Netscaler.
Azure MFA? How does it work?
With Azure MFA you have the option to use an additional second factor as authentication method in addition to the standard authentication (user name + password). This allows you to increase access to data in the Micrsosoft Azure Services and Microsoft Office 365.
Azure MFA therefore uses at least two of the following methods for authentication.
- Something they know (usually a password)
- One part you have (a smartphone or other device that cannot be easily copied)
- Something they are (e.g. fingerprint or face recognition
Enclosed you will find more information, in the article MFA is also described in more detail:
https://docs.microsoft.com/azure/active-directory/authentication/concept-mfa-howitworks
Versions and licensing of Azure MFA
I have picked out a KB article from Microsoft, here you can find a lot of information how to license Azure MFA.
https://docs.microsoft.com/azure/active-directory/authentication/concept-mfa-licensing
What are the requirements if you want to use Azure MFA?
Since we want to use Azure MFA on our Citrix ADC / Netscaler Azure MFA, we have some requirements that we have to fulfill first. I won’t go into all of them in detail, if you have any questions, feel free to send me a mail or contact me via LinkedIn or Twitter.
Requirements for Citrix ADC / Netscaler authentication with Azure MFA
- Your Citrix ADC / Netscaler (I am currently using the 12.1 55.18) should be already set up. Mine was previously configured for normal Active Directory authentication
- You should have configured a Netscaler Gateway or a Contentswitch with AAA Server. Incl. certificates and the site should be reachable via external connection
- A functioning Microsoft Azure Tenant with basic configuration
- Azure Active Directory Sync for the users from your Active Directory
- In your Azure client you should have Azure AD Premium P1 or P2, I use P2 for my article
- A MobileDevice, e.g. an iPhone with Microsoft Authenticator installed
- A server (I use Windows Server 2019) on which we can then install and configure our NPS server
Configuration of the Network Policy Server (NPS)
Here is an overview of how authentication via the NPS server to Azure MFA works

To set up my NPS server, I first need a Windows server (in my case Windows Server 2019), which I have integrated into the AD domain. Here I first install the server role “Network Policy and Access Server“.





Installation of the NPS Extension for Azure MFA
If the role for the NPS server has been successfully installed, the “NPS Extension for Azure” can now be installed. We need this extension so that our Network Policy Server can also communicate with Azure.
Here you can find the download link to the NPS Extension: https://aka.ms/npsmfa
Here you can find further documentation and instructions for the NPS Extension for Azure MFA: https://docs.microsoft.com/azure/active-directory/authentication/howto-mfa-nps-extension
I am now installing the NPS Extension on our NPS server.


If you have installed NPS Extesion for Azure MFA, please restart the server.
Connecting the NPS Server with Azure Active Directory
In order to be able to authenticate users with Azure MFA, the NPS server must be connected to our Azure Active Directory. We will do this in the next step. This is done using the Powershell Script that comes with the installation of the NPS Extension.
Start the script under the following path with the Powershell (please set the ExecutionPolicy to “Unrestricted” before and start the Powershell as administrator.
The Script is in the following path:
cd "C:\Program Files\Microsoft\AzureMfa\Config"
.\AzureMfaNpsExtnConfigSetup.ps1The script does the following:
- Create a self-signed certificate.
- Associate the public key of the certificate to the service principal on Azure AD.
- Store the cert in the local machine cert store.
- Grant access to the certificate’s private key to Network User.
If you are asked if you want to install the following components (NuGet Provider and the MSOnline Module” please confirm with yes.

The following information is requested when the script runs:
- Login (admin account) for your Azure Active Directory
- Password for the admin account in Azure Active Directory
- the Azure Teant ID
To find the Tenant ID for your Azure Active Directory, you have to log in to the Azure Portal(https://portal.azure.com) .
The Azure Tenant ID can be found as follows:

Here you can see how it looks like when the script is executed:



If the script has run successfully, your NPS is now connected to the Azure AD and we can configure the NPS server.
Configuration Network Policy Server
Please start the NPS configuration console first.

Now we first create a Radius Client. Since our Netscaler is the Radius Client in this case, we enter this client. We also assign a Shared Key. You need this key on the Netscaler for the setup of the Radius Server.
Create a new Radius Client on the NPS server.



Create the Connection Request Policies
We now create 2 Connection Request Policies.

Netscaler Azure MFA – No Forward
Please create the Policy as follow:
- Policy – ENABLED
- Type of network access server: unspecified
- Condition: Client IPv4 Adress = EURE NETSCALER NSIP
- Authentication: Local Computer
- Authentication Method: MS-CHAP v2
- Override Authentication: Enabled




Netscaler Azure MFA – Forward Request
Please create the Policy as follow:
- Policy – ENABLED
- Type of network access server: unspecified
- Condition: NAS Identifier: MFA
- Authentication: Local Computer
- Authentication Method: MS-CHAP v2
- Override Authentication: Enabled





Create the Network Policy
Now we are going to crate the Network Policy.

Netscaler Azure MFA (Network Polcy)
Please create the Network Policy as follow




Now that I have finished configuring the NPS server, I can perform the configuration on the Citrix Netscaler.
Configure the Citrix ADC / Citrix Netscaler
On my Citrix Netscaler I now create a Radius server for authentication. Please go to RADIUS in the Basic Policies.

Here I now create a server for the Radius authentication on my NPS server. Please do not forget the NAS ID. I have stored this ID further up on the NPS server.


Now I create a radius policy on the Citrix Netscaler.

Now I bind the Radius Policy to the authentication server. For the authentication with Azure MFA I only use the Radius Policy and bind it as Primary Authentication Policy.


Activate Azure MFA for users
In order for the users to be able to use Azure MFA to authenticate themselves on the Citrix Netscaler, Azure MFA must still be activated. You can activate Azure MFA for all users, groups or for individual users. To enable multi-factor authentication for individual users, please go to the Azure Portal and select User Management in the Azure Active Directory. There click on the button “Multi-Factor Authentication”.

To enable MFA for a user you can select the user in the window for multi-factor authentication and choose “Enable”.

That’s all there is to it. Now the user can log in to the Office Portal and configure MFA.
You can find the Office Portal at: https://portal.office.com
After the user has successfully logged on to the portal, the following message appears:

This must be confirmed with “Next”. Now the user can choose if he wants to log in with the second factor by “passcode” or by “push notification”.
Use Passcode for a User
In the first example I select the passcode to log on to the Citrix Netscaler with Azure MFA. Here you will also find how to change this to push notification.

The passcode must then be confirmed.

The phone number is also queried.

If all inputs were successful, you will get another password that you can use in the apps where MFA does not work. This includes Outlook App, Apple Mail and partly Microsoft Office. The password is your “app-password”. Please save it in a safe place.
With “Done” you can complete the setup of your passport code.

So, now we can test if on the Citrix ADC / Netscaler Azure MFA works.
For this purpose I select my Netscaler website, which I have secured with the authentication server.
There I get a login with username and password. As username I use the UserPrincipalName, which is the same as my Azure AD login.

When I login in, I get asked to enter my passcode.


If all credentials are correct, I will be directed to the desired website.

Now we take look at the Pushnotifications.
Use Pushnotification for Users with Azure MFA
Next, I would like to show you how the registration with Push works. Input your username and password. Now when you click on “Log in” the push notification in the Microsoft Authenticator App. Press Accept. Then you get logged in as desired.



Change the authenticationmethod for a user
If you want to change the authentication method for a user, you can do so through the Office Portal: https://portal.office.com
Go to the settings “My account”. There, go to “Security and Privacy” and select “Update your phone numbers used for account security” under “Additional security check

Here you can then select the desired option.
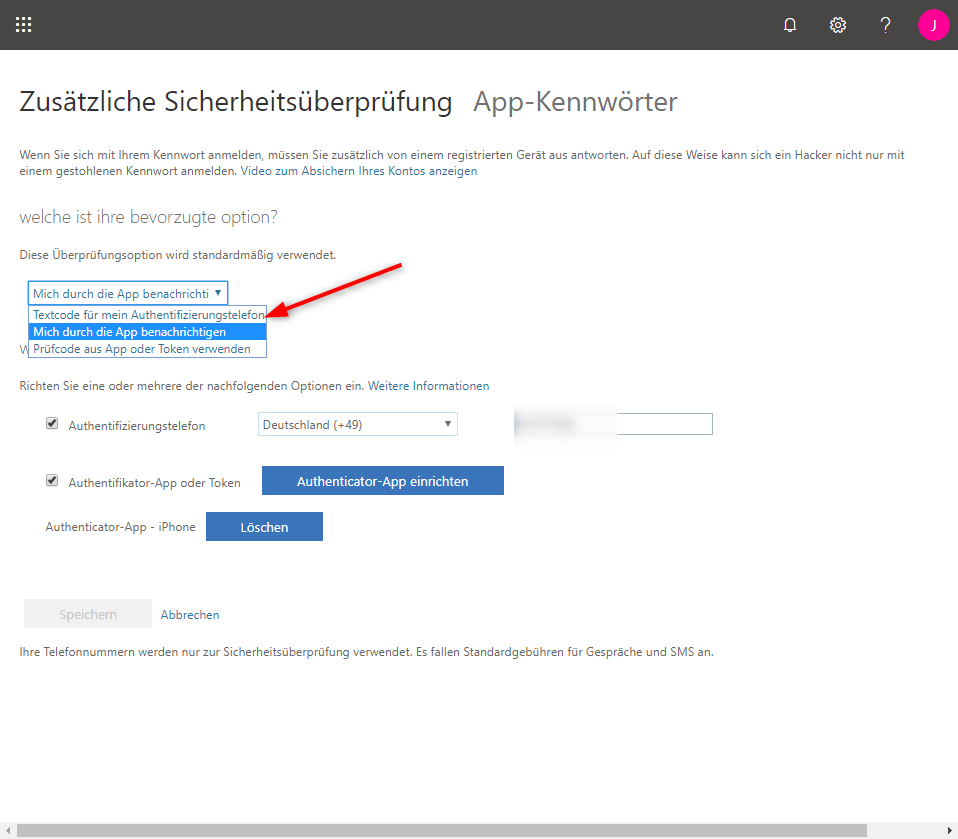
Click off “Save” and the “Check preferred option”.

You have to confirm the new method.
If everything works out, your method to authenticate is changed.

Troubleshooting Links
Here are some troubleshooting links that might help you in case of problems:
Frequently asked questions about Azure MFA:
https://docs.microsoft.com/azure/active-directory/authentication/multi-factor-authentication-faq
Troubleshooting Powershell Scripts for the NPS Extension for Azure MFA:
Additional Informations
Für alle von euch, die die Security Baseline von Microsoft anweden möchten, gibt es hier noch weitere empfehlungen von meinem CTA Kollegen Marco Hofmann. Nach dem Setzen der einstellungen, funktioniert die Authentication nicht mehr. Bitte schaut euch seinen Eintrag zu dem Thema im CUGC Blog an.
Link to the security baseline:
https://learn.microsoft.com/en-us/windows/security/threat-protection/windows-security-configuration-framework/windows-security-baselines
Link to Marcos Blog Post:
Citrix NetScaler Gateway: NPS Extension for Azure MFA Fails After Introducing the Microsoft Domain Controller Security Baseline
Thanks for this this worked like a charm!
Only thing is when you logoff the second password field is visible again, any idea how to fix that?
Hi Martijn,
nice to hear. Thanks for your comment. Can you please check your web browser. I think you mean if you logoff from storefront server.
Maybe there is a problem with the refresh of your browser. I checked it with Google Chrome, here the session is logged off normal and no field is showing up again.
Tom
Hi Tom,
It is great article and exactly what I have been looking for. However I got one question. We don’t have Azure AD Premium plan but we have O365 E3 subscription which comes with MFA.
Can I set up the same with O365’s MFA only?
Thanks in advance,
Netlynker
Hi, you can check the versions if it is included under: https://docs.microsoft.com/azure/active-directory/authentication/concept-mfa-licensing
I think with normal o365 e3 it will not work. But with EMS or Microsoft 365
Hi, great article. It’ possible in this configuration using Radius as Secondary Authentication, with user AD as principal?
yes, you can. the question is for which usecase. normaly you also can use UPN instead of SAMAccountName. You only have to delete the logindomain in the sessionprofile for SSO.
Hi Thomas, great article.
Is this the only way to implement this?
On a Citrix article, they are referencing two other options (I might be misunderstanding the article) “Azure AD and Azure MFA” and “Azure AD pass-through authentication and Azure MFA” which seem to be modern versions as the method you reference doesn’t support the Azure AD conditional access policies.
https://docs.citrix.com/en-us/advanced-concepts/implementation-guides/citrix-gateway-microsoft-azure.html
Hi,
normaly you can use Azure MFA as I explained to authenticate with User and Password, if user is activated for MFA, you will get asked for push or code. It´s dynamic (user configuration).
Azure AD pass throug means, if you have a user, which is not activated for MFA, normaly the authentication is not permitted, with pass through, you can authenticate with the NPS Server, like a DC on Active Directory.
Hi thomas
We are facing a problem has already one week. no good yet.
we did all the steps, but we have an error on the NPS server:
“NPS Extension for Azure MFA: NPS Extension for Azure MFA only performs Secondary Auth for Radius requests in AccessAccept State. Request received for User xxxxxx with response state AccessReject, ignoring request”
At netscaler side, we just need only primary authentication (Radius) even we are using desktop (web) and mobile receiver? how about LDAP? we didnt anyumore?
i´m very confused.
Thanks a lot!
You only need the nps for authentication. Seh as Primary. Have you assigned mfa for the User in Azure ad?
Yes. It´s ok in Azure ad.
yesterday we able to connect at netscaler with just primary (Radius). Phone app request to aprove and so on.
I dont know wy, but we had to set “Accept users without validating credentials” on Authentication at Connection Request Policy (Foward Request). Before set this step, for some reason, Netscaler was saying “Wrong username or password”.
But with this set, any type password is accept.
Today we gonna try put LDAP (primary) + Radius (Secondary) and add a Rewrite policy to hide token filed. (netscaler).
its seems NPS is not validating the LDAP windows credential from netscaler with just Radius on Primary Authen.
Hi Rodrigo,
I think there is a problem with your NPS configuration. That normaly should work. You only need a primary authentication for this scenario. Please check your Certificates which are created during the setup of mfa plugin. There only should be one (delete the others). Please also check the permissions on the private key of the certificate. If you need further assistance, feel free to reach me over the contact form on my website or via Twitter PN @thomaspreischl
Hi I see the same problem. Looks like AD authentication does not work. When I check the accept users without validation it works. It can’t be a certificate problem otherwise the mfa would not work at that point. I am not sure how in the configuration AD authentication is triggered towards on prem AD. We don’t have our passwords synced to AAD but I’m not sure what that would have for impact on this. I would expect none.
Hi, I have the same problem. I have to set “Accept users without validating credentials” to get it working. I see a reject on the audit log on the DC that password is incorrect, but its not because when i do above setting authentication works. It also works fine with ldap as primary and radius as secondary but then i have a problem with my workspace app wanting a second passcode
You only have to use NPS(MFA) as primary authentication. It is not required and the setup is sending all requests to NPS. If you want to use LDAP. You have to configure nFactor.
This work great for us too, thank you very much!
My question is is there a way to create MFA exception for certain IP ranges? We’d like to exclude internal network and partner network to MFA for user experience and license cost reasons. We have not figure out a way to successfully configure MFA bypass with this setup.
Hi Tom,
Thank you :).
Yes, you can use nFactor to check your IP Ranges and forward to NPS or not. I am working on a blog post over this scenario. Came back next weeks and you will get mor information or follow me on twitter and you will also get the link for the post.
Hi Thomas,
Is there a way to whitelist a security group for authentication instead of accepting all accounts?
Hi,
you can use nfactor to check the security group first. After that you can choose the action for the group, block, forward to NPS with MFA or another 2nd factor.
I hope this will help you, if not, we also can talk or you can mail me directly
Hi Thomas,
first of all I want to thank you for your easy to understand explanations.
Unfortunately I have a problem for which I have not yet found a solution. I have a small group of users who are not MFA enabled yet. With MFA the login as secondary authentication via the NPS server works without any problems. Users who do not yet have MFA cannot log in. In this case Microsoft suggests setting the registry entry REQUIRE_USER_MATCH on the NPPS server to false so that users without MFA can also log in. However, this does not work. Do you have an idea what could be the reason for this?
Thanks a lot
Hi,
you can Enable NPS Server to authenticate all Users. You can use the REQUIRE_USER_MATCH.
https://docs.microsoft.com/de-de/azure/active-directory/authentication/howto-mfa-getstarted
You have to use FALSE as Setting and restart your NPS Server
This document is so helpful. We have installed the NPS server and MFA is not getting triggered. We have a specific use case where we want to bypass the MFA requirements for people who comes specific Internet IP address ranges. Do we have an option to configure it this way as our NPS servers are placed in the domain.
Hi, you have to use nfactor. With nfactor you can use ldap for specified ipranges and MFA as default.
You only need to use NPS. Yes, LDAP is also done via NPS
Hi Thomas,
Thank you for your efforts, I have a scenario to integrate Azure MFA with Palo Alto Global Protect client, can I use the same procedures above, or may the configurations differ from vendor to vendor.
Hi, I think you can use my setup even for that. I think you will give it a try
Do you know if there is a way to change the messaging if the user is not registered yet? I get the 4001 message i could change that but that would change for all 4001. I just want to send a message with a link to office.com to register if the user hasn’t resisted yet.
Hi Kevin, I would do the mail sending with microsoft flow. There you can check if MFA is allready active for the user. You also can authenticate users which are not using a second factor (only Password) with NPS.
Hi!
Great article!
When using push, do you know if it is possible to give the users some sort of notification so they know that they need to accept the prompt on their phone?
Hi, that is possible with nfactor implementation. I will provide a new article for this in the next few weeks. If you cant wait for this, please send me an email
Hi Thomas,
Did you get round to writing this article? Couldn’t find it but we are also interested in this.
Cheers
I ended up trying something similar to what is described here: https://jkindon.com/2018/03/05/azure-mfa-nps-extensions-with-netscaler-nfactor-authentication/
It is not the interactive prompt I was hoping for, but at least we can add a descriptive text before the credentials are sent.
For an interactive solution you have to use azure MFA or Okta
Hello Dre, can you please share your code for this?
Thank you!
Hi,
why do you setup two connection policies? They both are configured to use local authentication and differ only in the conditions. Since the connection policy “Netscaler Azure MFA – No Forward” is the first in the processing order and the condition mets, “Netscaler Azure MFA – Forward Request” is never used, right?
You wrote “Please go to RADIUS in the Basic Policies” but the screenshot shows *ADVANCED* Policies. I think no one should start with “Basic Policies” anymore. They are deprecated and Citrix has announced to remove them with version 13.1. Do you have an example, how to configure this with advanced policies instead?
best regards
Hi Kai,
my lab vm was running on 12.1. because there are many issues on 13.1 in the time the post was written.
I have 2 NPS policies, because I don´t want to forward the requests, which are comming from ADC to monitor the connection to NPS. That´s the reason why you should use 2 conditions.
To migrate the policies from classic to advanced is not a big thing, if you need help, please send my an email or connect to me over twitter.
I have completed all of the steps above and this works great when you are using the Web Portal to gain access. But when attempting to use and configure the Receiver for access, I can authenticate, I can log in one time and then after closing the Receiver or waiting for the reauthentication process, it fails to login. You have to delete the Store and re-add it each time you want to use it. Has anyone been able to get the Receiver portion to work? With other MFA apps like Duo, they had the authentications policies split to work but this appears to combine the policies together.
Hi,
have you created a new storefront or a new gateway on adc? You only have to use the MFA Auth, no LDAP additional or something.
What you describe happens normally, if at the 2nd time connect, another gateway as default adc gateway is stored in the storefront. Then your client goes to that and not to the new one with mfa
Hi,
the manual works so far. Perfect!
One thing which came up: When I reject the message in Microsoft Authenticator, I´m logged in to Citrix Gateway. – That should not happen…
Hi again,
I managed it to work. The problem was that there was a LDAP-Policy in the ADC-Configuration. After I rearranged the policies, it worked as desired.
Perfect, nice to hear you got it work.
If you have any questions, please feel free to get in contact with me. Also in german 😉
Do you know if Azure NPS plugin works with multiple Azure tenants or we need separate NPS servers for other Azure tenants?
Hi, you must install multiple NPS. Even if you wantto use NPS for different functions. If you want to authenticate on netscaler/ ADC against multiple NPS you can use nfactor or cascade authentication (same as different ldaps)
Hi Thomas,
I have this setup and working (partly) in our POC. Not all the users in our environment are MFA enabled. MFA enabled users are logging on successfully. But the users without MFA enabled/configured (e,g, shared accounts) are failing to authenticate. We are getting RADIUS Authentication Failure (691).
******
/usr/home/build/adc/usr.src/netscaler/aaad/radius_drv.c[2012]: process_rad_reject 0-82131: RADIUS auth: Processing RADIUS reject for user test.user, MS-CHAP error ERROR_AUTHENTICATION_FAILURE (691)
/usr/home/build/adc/usr.src/netscaler/aaad/radius_drv.c[2188]: process_radius 0-82131: RADIUS auth: Authentication failed for user GB999.teststore from server x.x.x.x – Invalid Credentials
******
Do all the users have to have MFA enabled for this work or we can setup separate policies to authenticate non-MFA users?
Regards.
Also want to know the differences between two connection policies ‘forward’ vs ‘non-forward’ other than separate conditions (IPs vs NAS ID), they’re both identical. Both my MFA and non-MFA authentication are using ‘forward’ policies. Could this be an issue?
The Azure NPS extension broke all my existing NPS RADIUS clients. Uninstalled the Azure extension and all is ok again. Does this not work with other RADIUS clients using regular AD auth?
Check out our Shopping Centre Design and get help from professional Architects! We provide only unique Shopping Centre Design that meets all of your requirements.
Citrix ADC / Netscaler Azure MFA Authentication – Next stop. Next level.
jgpyklrdxj http://www.gn5zfduoq00j4513d61gz493h82t5e8as.org/
[url=http://www.gn5zfduoq00j4513d61gz493h82t5e8as.org/]ujgpyklrdxj[/url]
ajgpyklrdxj
Portable Anaesthesia Machine
3Pin Multi-function Socket Universal Socket
スーパーコピー時計級品優良店
2 Pie Baby Blanket and Travel Pillow Blanket Gift Set
素晴らしいスーパーコピーブランド偽物級品専門店
Where To Buy Goji Berries
if AD user password expired the azure MFA extension get failed to auth
Hi Thomas, great write-up! Could you clarify how were you able to get rid of “password” label in case of text message/SMS-based authentication? I used something very similar using nfactor, however “password” label is shown against “Enter Microsoft verification code” which is not ideal.